The Platform | Measure ROI · Govern Risk · Custom KPIs · Monitor AI · Shadow AI
Find and Control the AI You Don’t Know About
Discover. Assess. Govern Unauthorized AI Usage.
The Shadow AI Problem
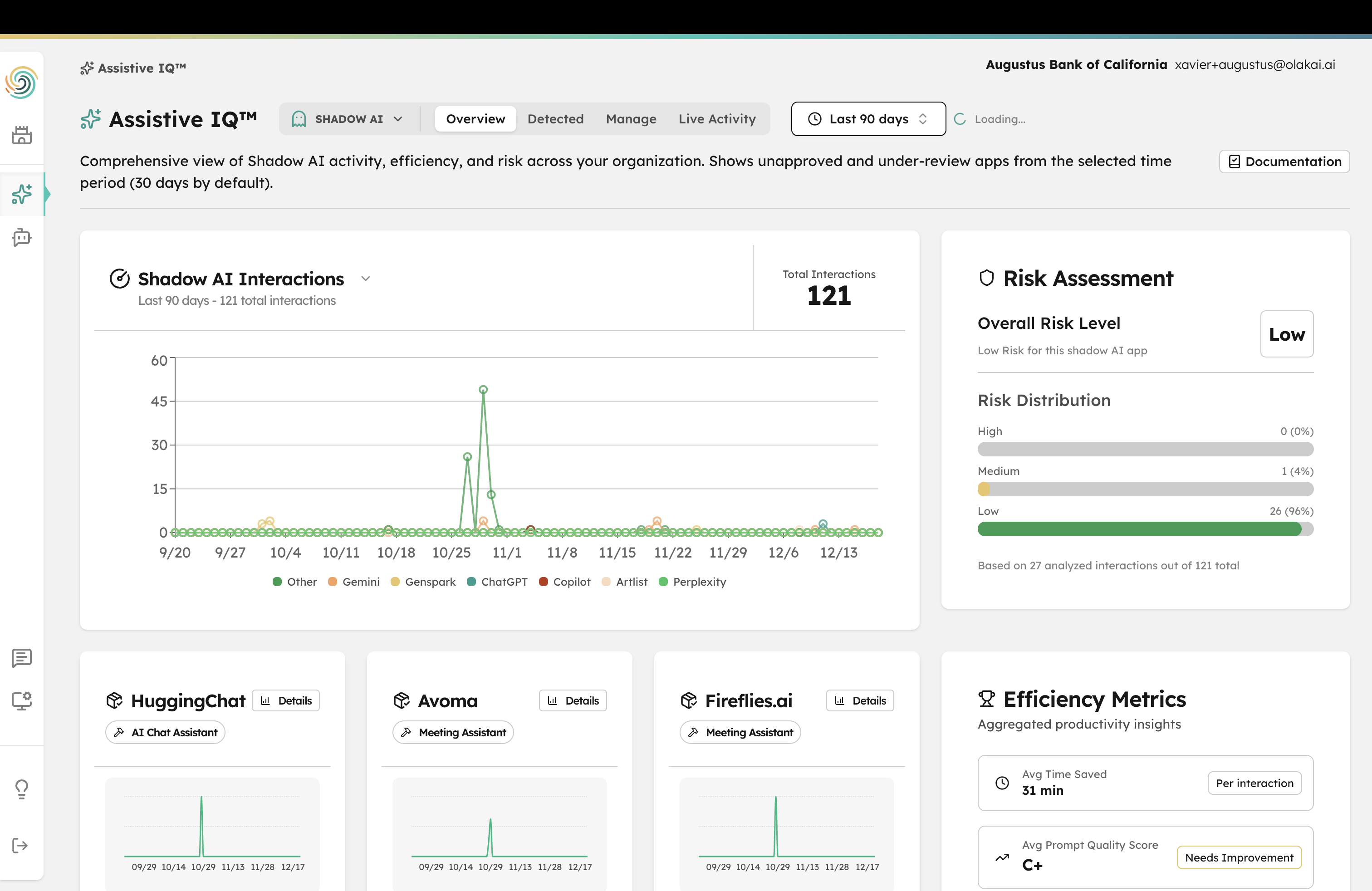
Your employees are already using AI—the question is whether you can see it. Over 60% of enterprise AI usage happens outside IT’s visibility. Employees adopt ChatGPT, Gemini, Claude, and dozens of other tools on their own, feeding them customer data, source code, and financial projections with zero oversight.
Every unauthorized AI tool is a potential data leak, compliance violation, and security incident waiting to happen. And you can’t govern what you can’t see.
Invisible tools
Employees use browser-based AI tools that bypass your security stack entirely—no installs, no approvals, no visibility.
Data leakage
Sensitive data flows into unvetted AI models with no DLP controls, training opt-outs, or retention policies.
Compliance exposure
Unauthorized AI usage violates data handling policies, creating regulatory risk you discover only during audits.
Zero inventory
No one knows how many AI tools are in use, who’s using them, or what data they’re processing.
The Solution
Shadow AI You Can See and Control
Automatically discover every AI tool in use across your organization, assess risk in real time, and enforce governance policies—without blocking the innovation your teams need.
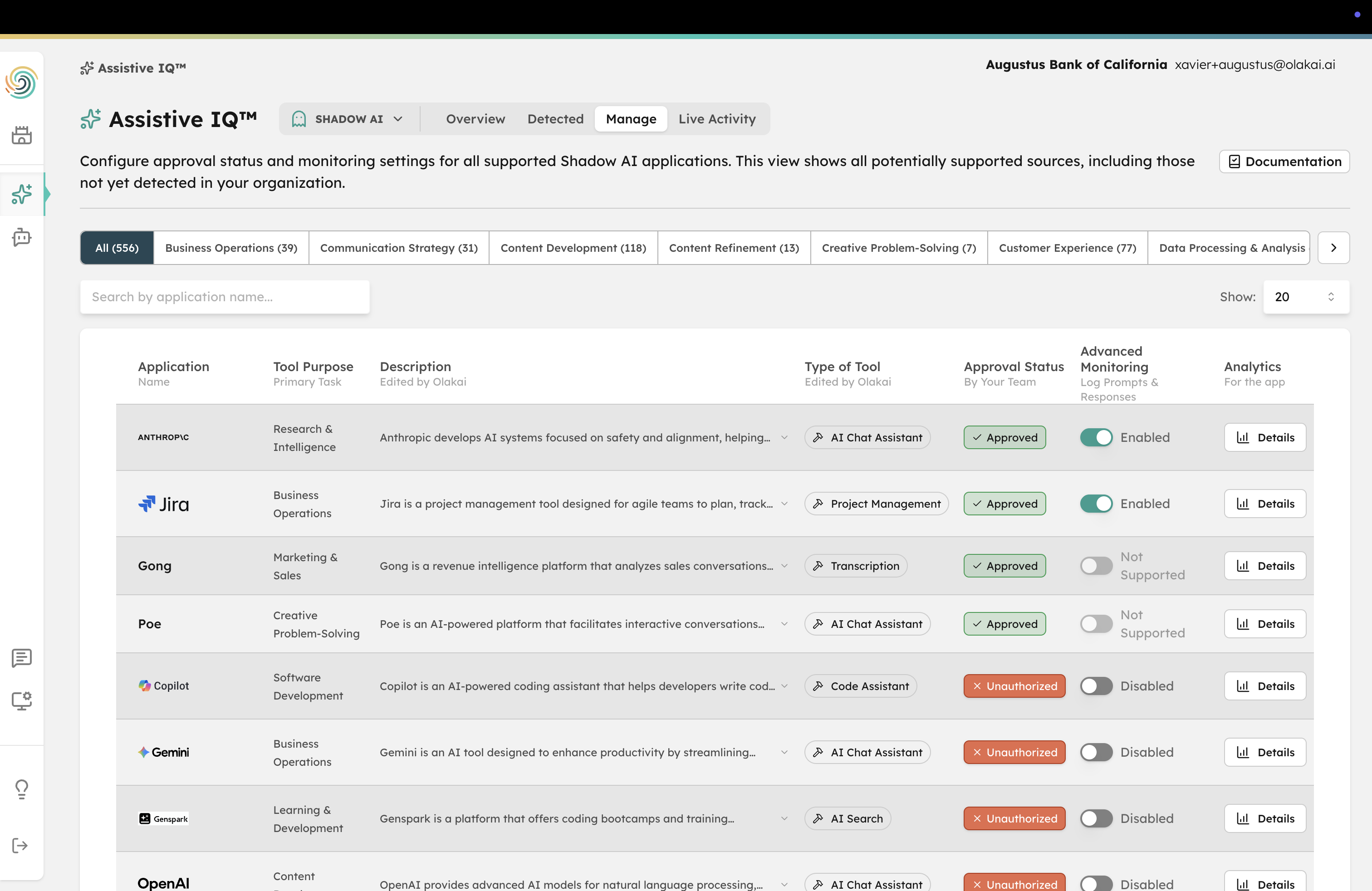
Auto-Detection
Continuously scan for unauthorized AI tools across browsers, APIs, and integrations. Olakai discovers new AI services as employees adopt them—no manual inventory required.
Risk Scoring
Every detected AI tool is automatically scored for data sensitivity, compliance exposure, and security risk. Prioritize remediation by actual impact, not guesswork.
Approval Workflows
Route newly detected AI tools through approval workflows that match your organization’s risk tolerance. Approve, monitor, or block—with full audit trails for every decision.
Usage Analytics
See exactly who is using which AI tools, how often, and what data they’re sharing. Identify high-risk usage patterns and enforce data handling policies automatically.